ICS Stallions
OT Cyber Defense Services
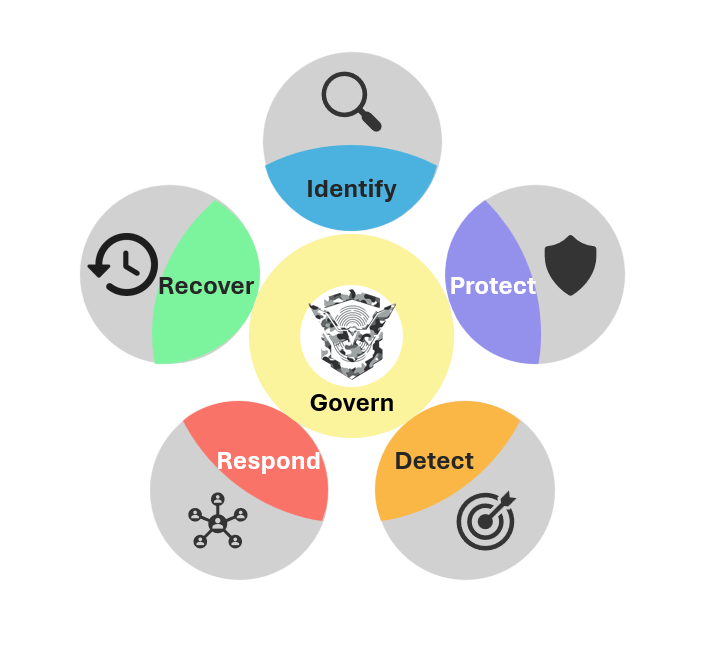
Integrated Cybersecurity for ICS, OT, IIoT, IoT, and IoMT Environments
Fourth Command extends cybersecurity beyond traditional IT environments, integrating robust protection for ICS/OT, Industrial IoT (IIoT), IoT, and IoMT technologies. Our OT cyber defense framework is built upon our specialized services—Basecamp, Knights, Black Phoenix, and Black Arrows—ensuring a comprehensive, risk-based approach to securing critical infrastructure. By combining advanced threat intelligence, security testing, and real-time detection and response, we safeguard industrial environments from cyber threats that could disrupt operations. With the growing convergence of IT and OT, our tailored security framework enables organizations to proactively defend against evolving cyber risks, ensuring resilience, compliance, and operational continuity.
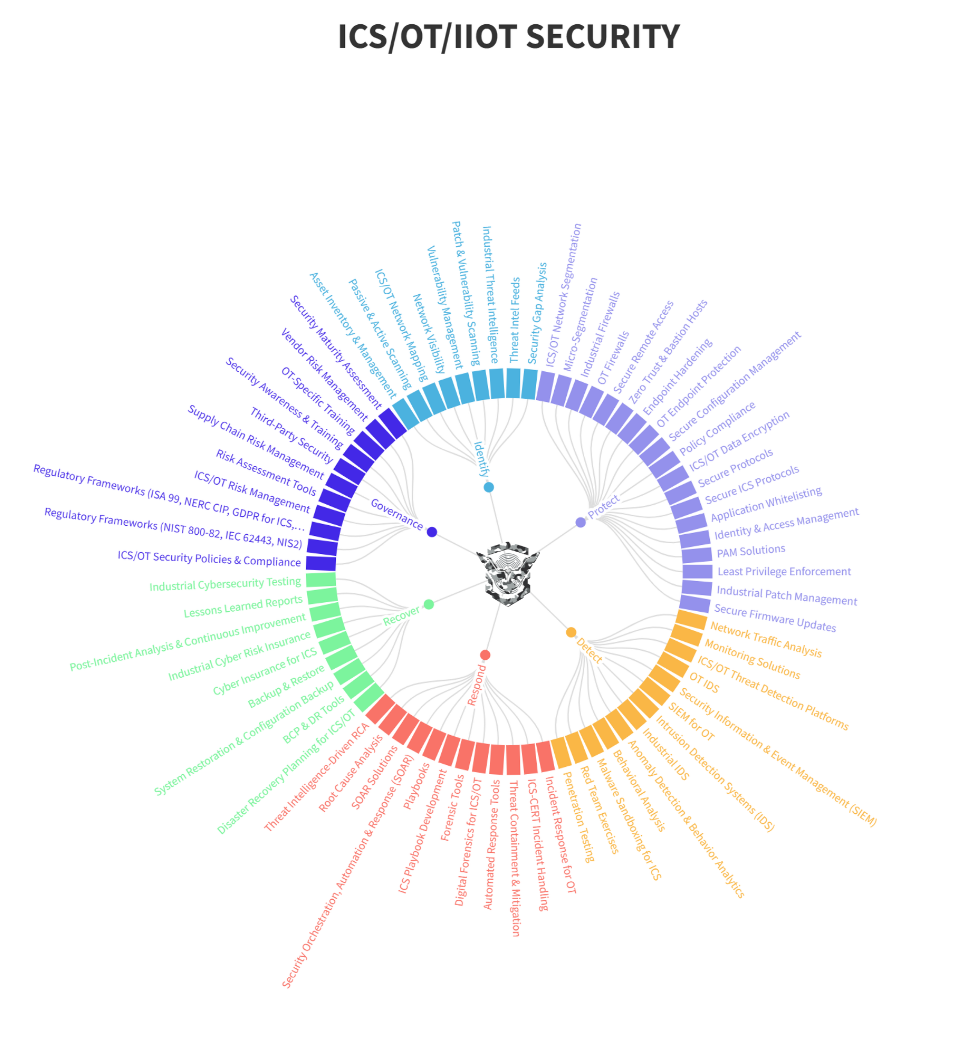
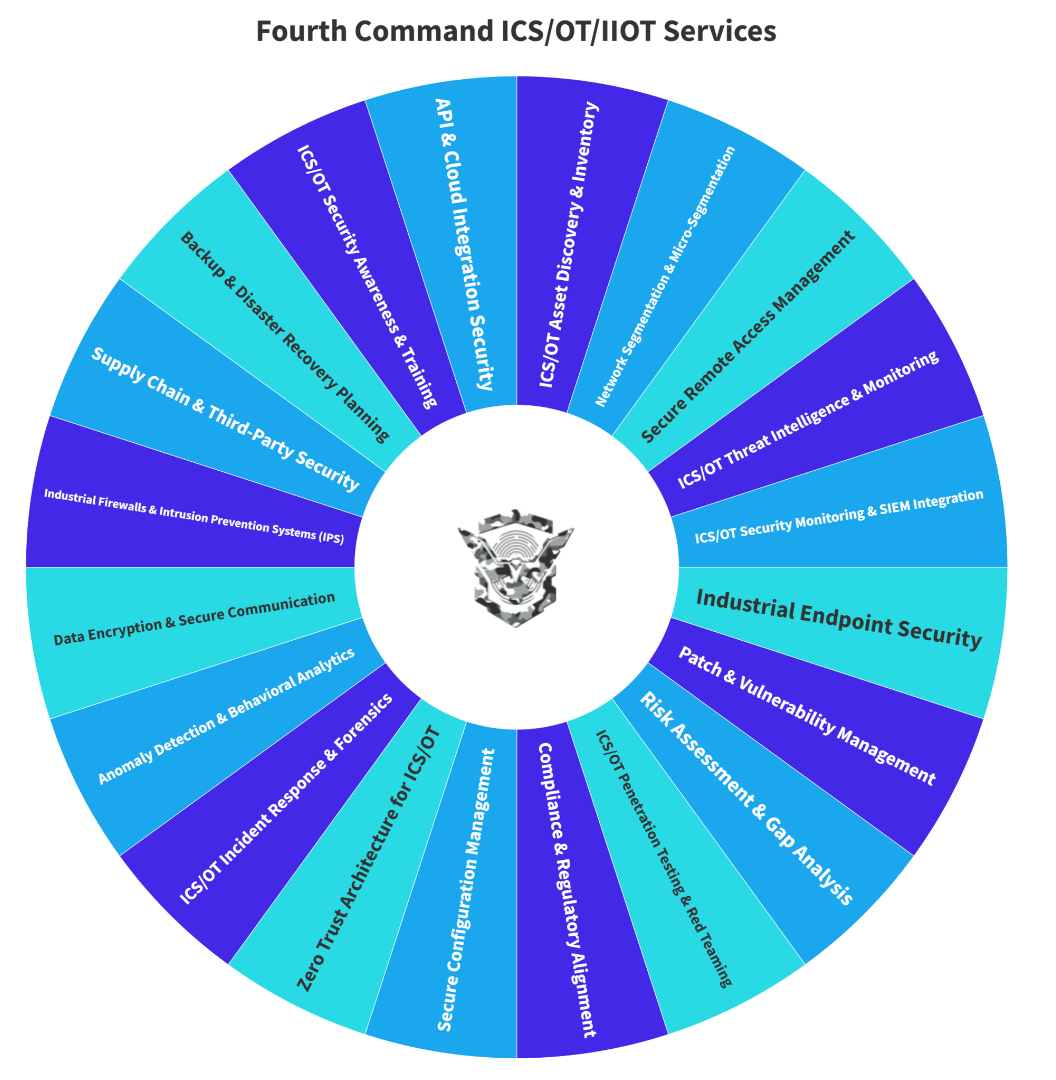
industrial control systems(ICS)/operational technology(OT)/iiot
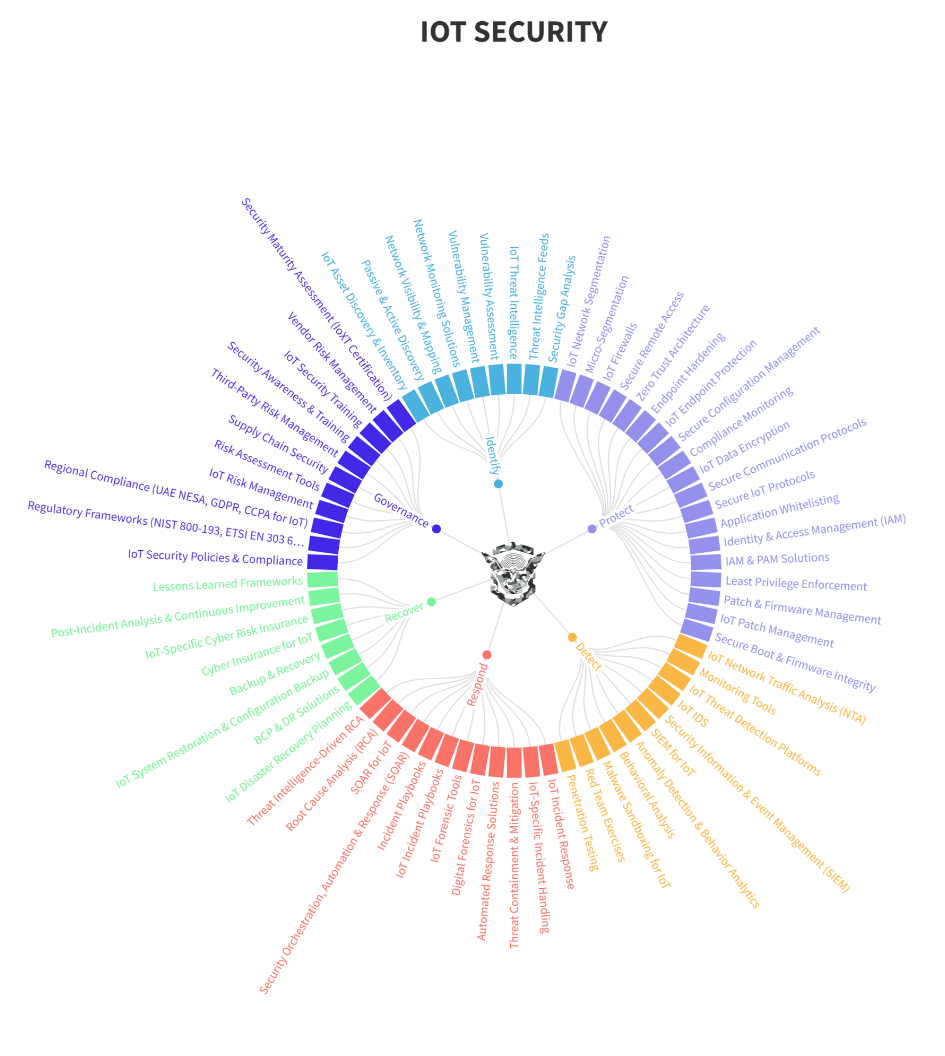
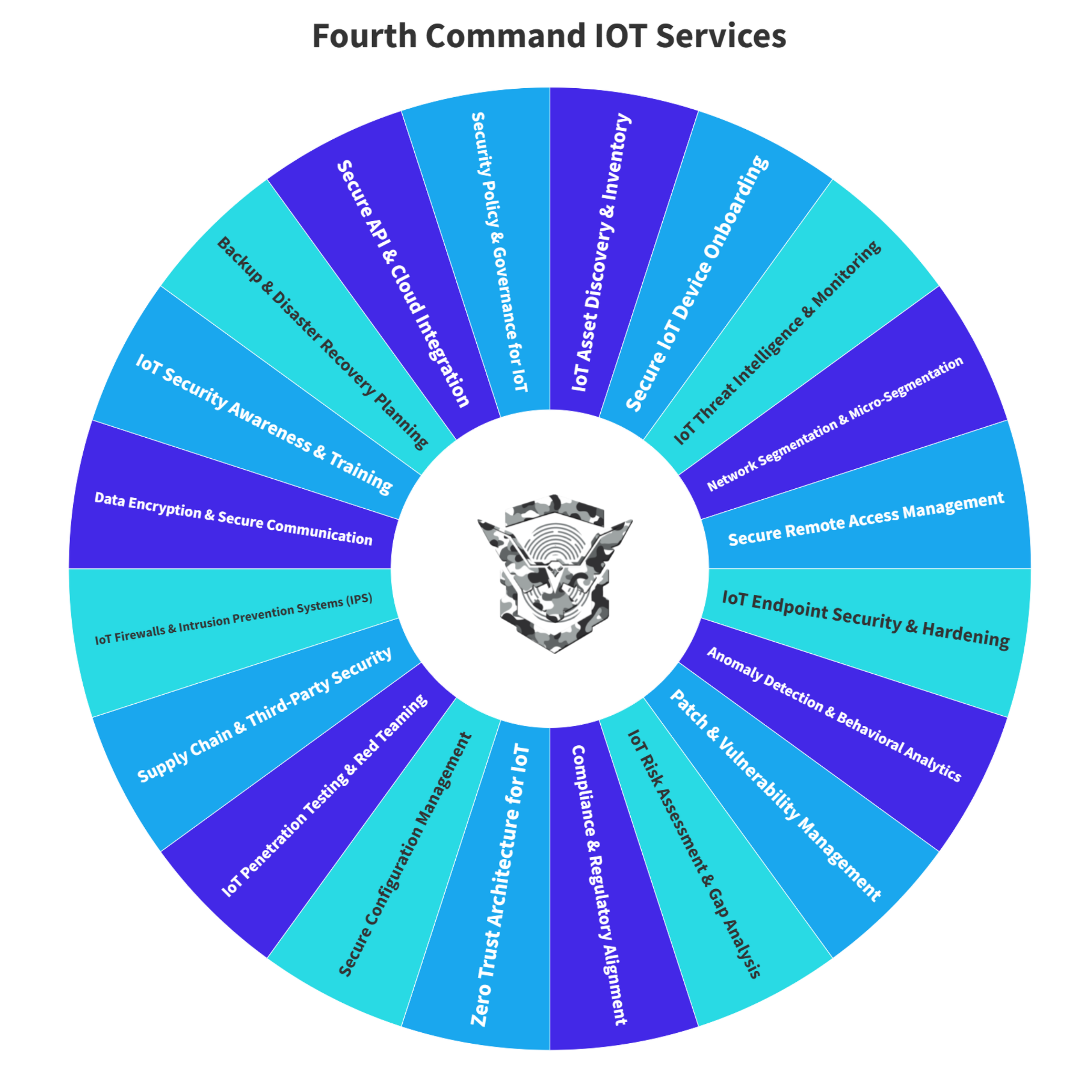
internet of things(iot)
internet of medical things(IOMT)
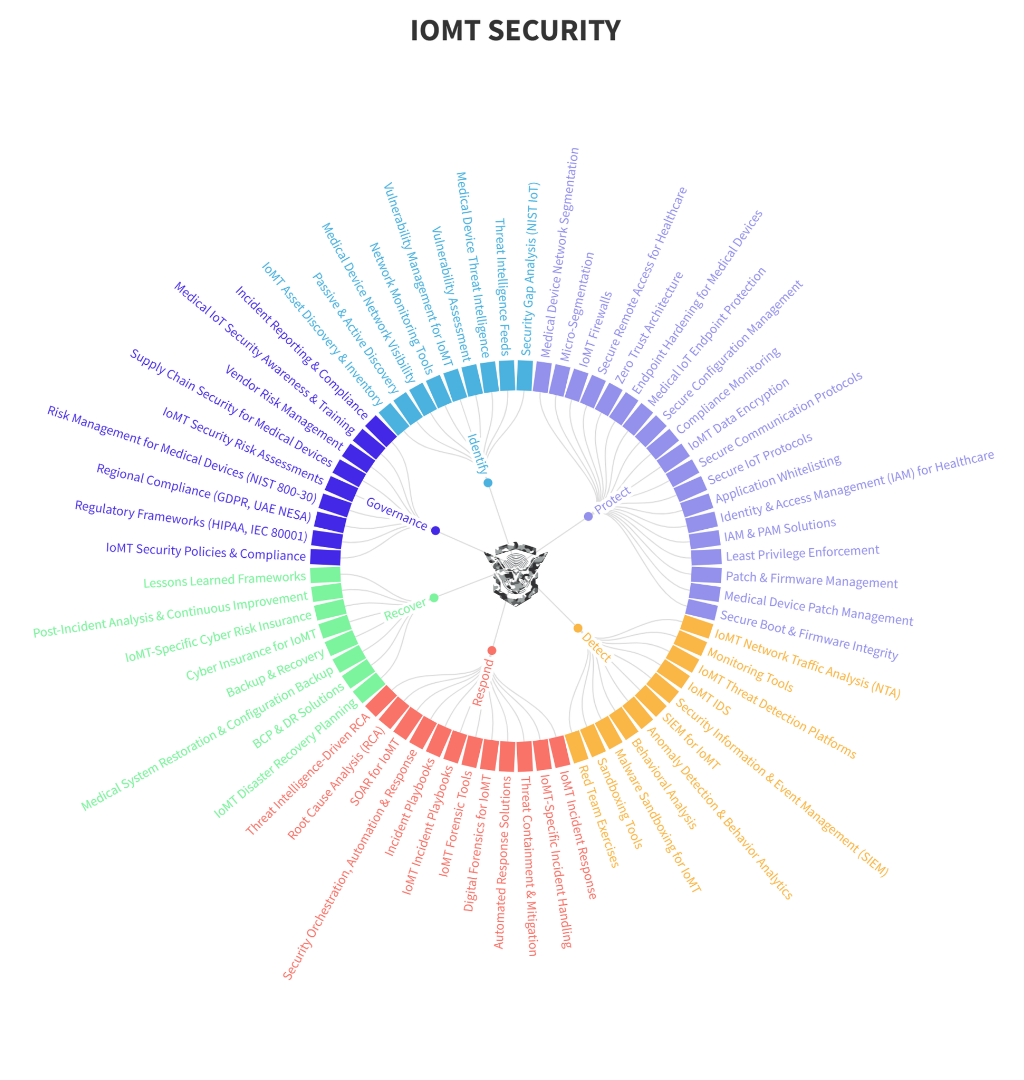
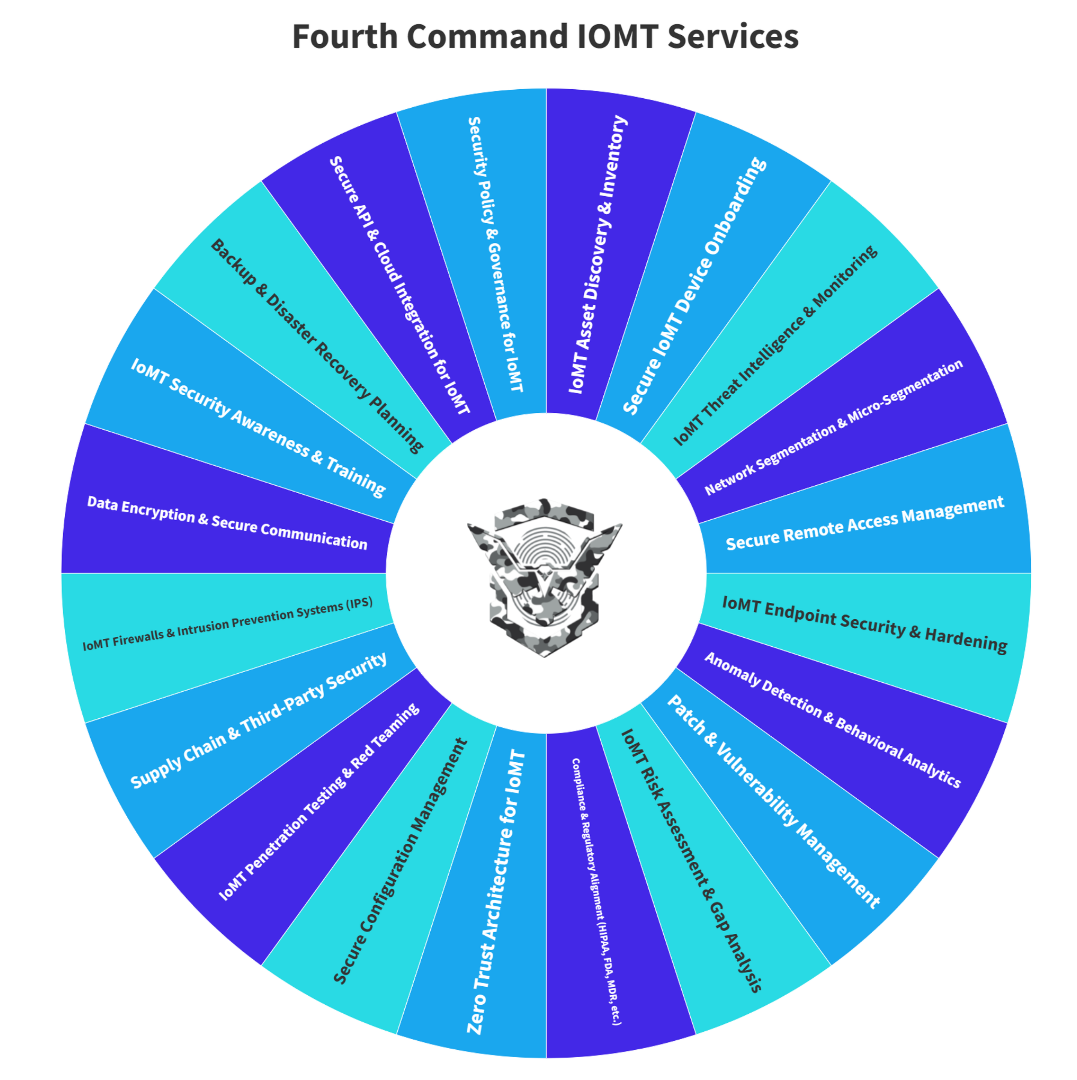
Industry specific critical infrastructure cyber defense