
Garuda
Cyber Range and Trainings

Garuda: Cyber Defense Academy

Higher Education

Fully Equipped with
Hands-On Skills
Experienced with most
Recent Attack Vectors

Proficient with
Commercial Tools

Prepared for the Realities
of a live attack

Cyber Lab
Fundamental Skill Development
Learning Path
End to end, curved programs
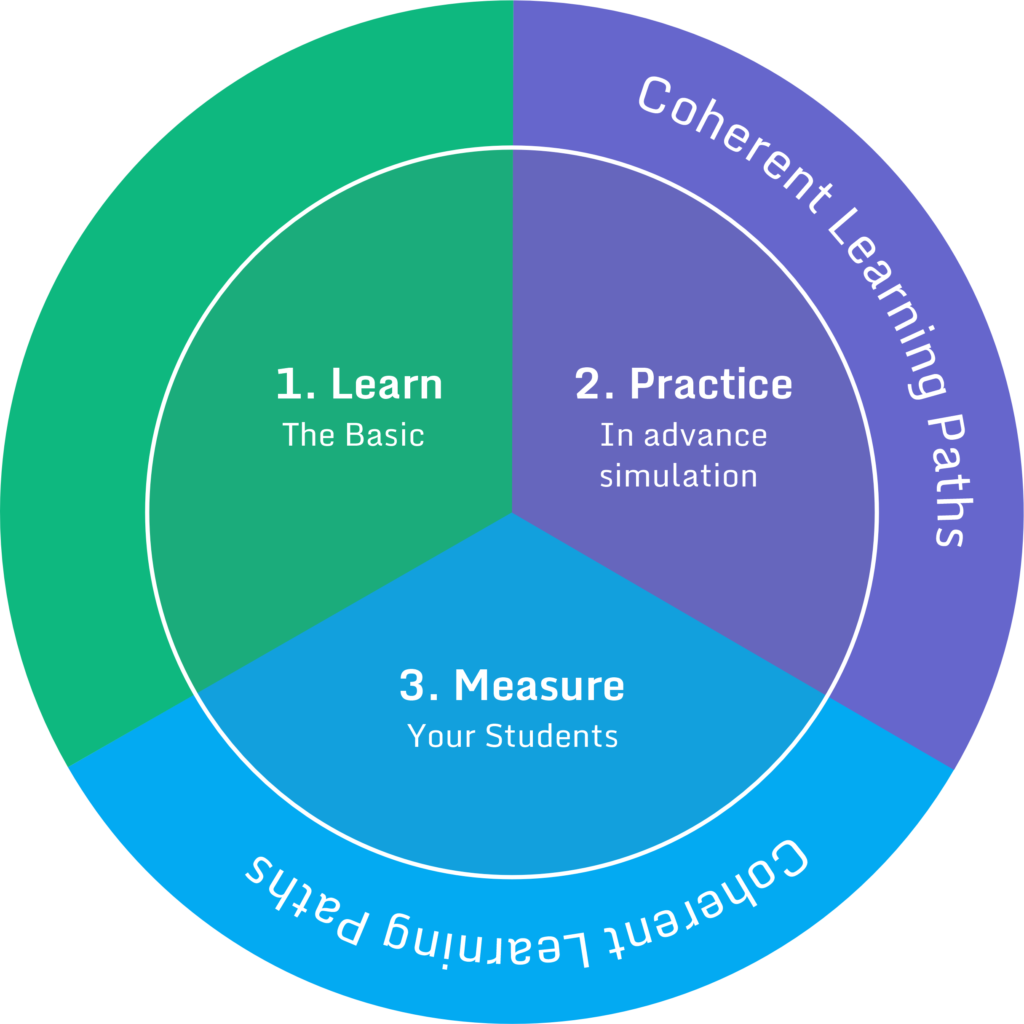

Cyber Range
Advanced courses,
Real-world Simulations, research

Assessment Center
Automated students
evaluation
and program tracking
Government

time to response

candidate selection

Operations
Workforce Framework for Cybersecurity
NICE Framework
The Workforce Framework for Cybersecurity, commonly referred to as the NICE Framework, is a nationally focused resource to help employers develop their cybersecurity workforce. It establishes a common lexicon that describes cybersecurity work and workers regardless of where or for whom the work is performed. The NICE Framework applies across public, private, and academic sectors.
Distinct areas of cybersecurity work
Work Roles (52)
Categories
Analyze
Collect and Operate
Investigate
Operate and Maintain
Oversee and Govern
Protect and Defend
Securely Provision
Courses
- nmap
- Wireshark
- Metasploit
- iptables
- Apache
- pfSense
- Kali Linux
- Autopsy
- tcpdump
- SCADA
- Sleuth Kit
- MySQL
- BIND
- P2P Marshal
- Splunk
- OSSEC
- Nikto
- FreeBSD
- Hydra
- SSLScan
- OpenSSH
- Burp Suite
- Zeek
- Security Onion
- hping3
- Denial of Service (DoS)
- OWASP-ZAP
- ExifTool
- setoolkit
- sqlmap
- Rekall
- FOCA
- AppArmor
- SELinux
- MariaDB
- FTK Imager
- tcpreplay
- Volatility
- OllyDbg
- Jenkins
- GRR Rapid Response
- RegRipper
- Cuckoo Sandbox
- Elastic Stack
- Vega
- unicornscan
- Colasoft Packet Builder
- Sguil
- Man in the Middle Attack
- phishing
- Snort
- VyOS
- OpenVPN
- Windows Server
- Active Directory
- fping
- wfuzz
- rsyslog
- nxlog
- logwatch
- fail2ban
- OpenVAS
- SPARTA
- OpenSSL
- WordPress
- Heartbleed
- NST
Securely Provision
Architecture
Securely Provision
Data Administration
Network Services
Systems Administration
Protect and Defend
Cyber Defense Infrastructure support
Incident Response
Vulnerability Assessment and Management
Analyse
Threat Analysis
Exploitation Analysis
Collect and Operate
Cyber Operations
Investigate
Digital Forensics
Trainings for International Certifications
Fourth Command has a niche training product on international certifications. Our next generation training methodology gives a more practical approach for employees and students to use the certifications in their ongoing career programs. Our trainings are conducted by certified industry experts, with lab exercises and exam prep and testing materials.








