
Panthers
Security Architecture as a Managed Service
Your security is our passion! We secure Enterprise Digital Design:
Panthers is the Region’s First Security Architecture as a Service. Partner with us.

Industries failing to comply with proper security architecture approach
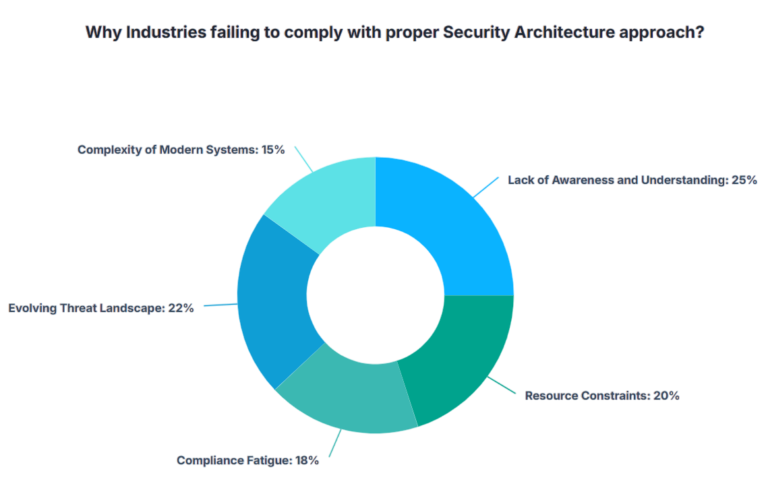
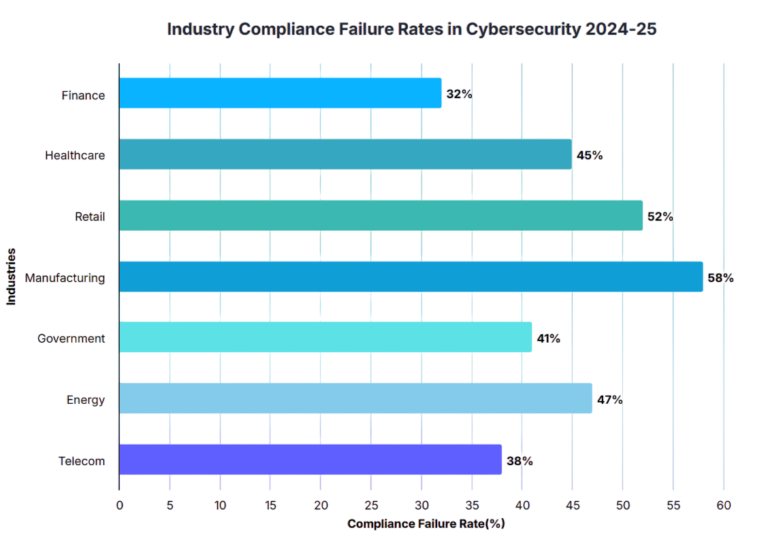
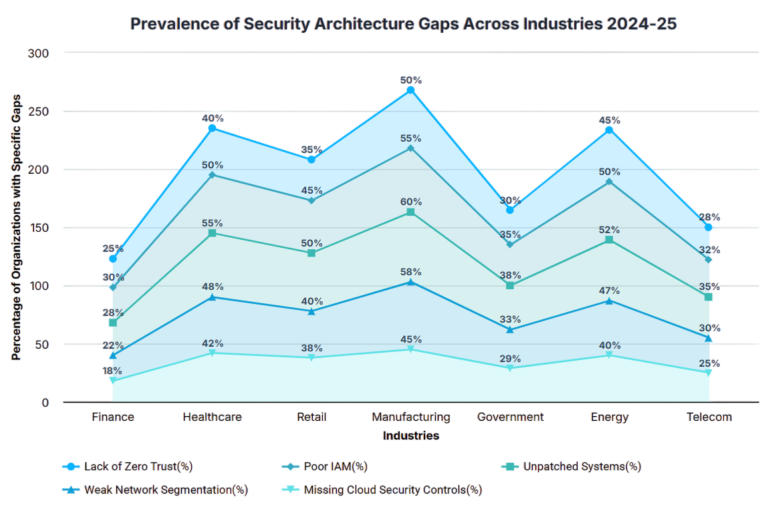
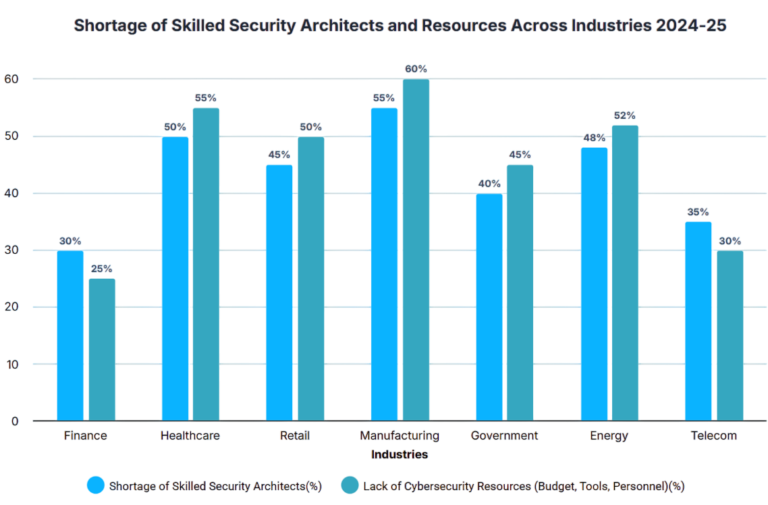
Security architecture standards
Zero Trust Architecture (ZTA) – Assumes no implicit trust and verifies every access request.
SASE (Secure Access Service Edge) – Integrates network security and wide-area networking in the cloud.
SABSA (Sherwood Applied Business Security Architecture) – A risk-driven, business-focused framework aligning security with business objectives.
TOGAF Security Architecture – A structured framework for enterprise security integration within IT architecture.
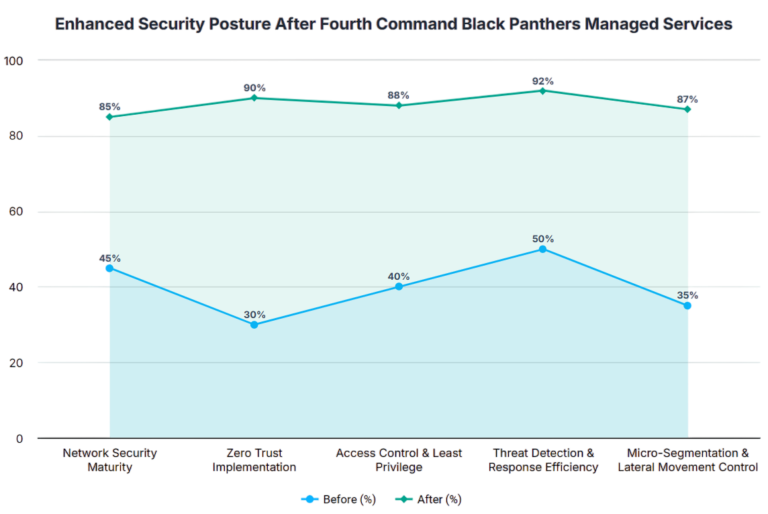
Security Architecture Managed Services
Fourth Command Security Architecture Managed Services offers specialized consulting designed to safeguard your enterprise at every level. Our seasoned experts—with a minimum of 10-15 years of industry experience—leverage the most suitable security architectures to ensure that your business requirements and applications remain secure, while continuously enhancing your internal security resilience.
Our strategic approach to security architecture consulting is built around three core pillars:
- Digital Transformation Security: We embed robust security architectures into your digital transformation initiatives, ensuring that new technologies and platforms are secure by design.
- Cyber Resiliency: We enhance your internal security posture to withstand evolving cyber threats, ensuring your systems remain robust and resilient against potential breaches.
- Supply Chain Security: We implement targeted measures to improve the security of your supply chain, mitigating risks associated with third-party integrations and external dependencies.
By integrating these elements with the Zero Trust Architecture concept, Fourth Command provides comprehensive security architecture consulting as a managed service. Our approach is tailored to the unique needs of each organization, ensuring that every aspect of your enterprise’s security framework is robust, adaptive, and future-proof.
- Expert consulting on Zero Trust Strategy and implementation.
- Managed security architecture services for continuous protection.
- Managed service for Secure business application design with architecture and requirement analysis.
- Enterprise security architecture maturity assessments.
- Strategic roadmap consulting for long-term security resilience.



