
basecamp
Cyber Defense Transformation Program

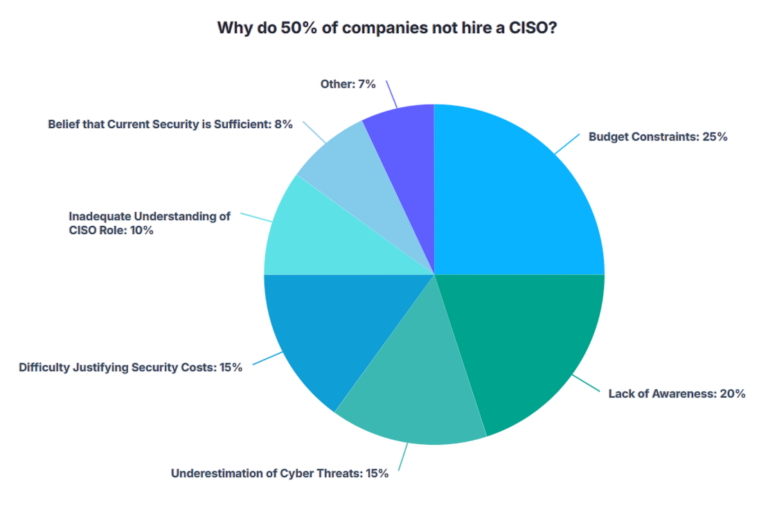
50% of Companies Operate Without a CISO—Are You Taking the Risk?
BASECAMP

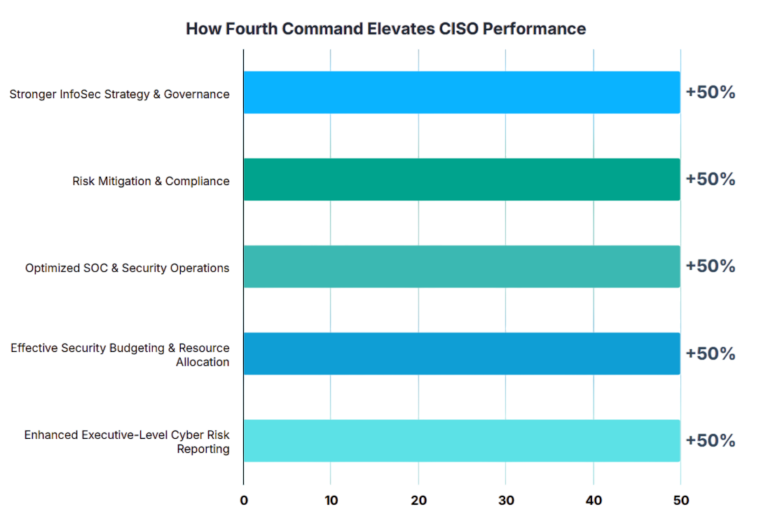
Fourth Command 24/7 Confidence for Board, CIO, CISO and Cyber Security Executives.
- Information and Cyber Security Enterprise Program/Department Development
- GRC Consulting and Program Development
- Enterprise Cyber Threat Profile Development
- Enterprise Cyber Risk Quantification and Cyber Security Budget Program Development
- Enterprise Cyber Asset Attack Surface Management Program Development
- Enterprise Vulnerability Management Program Development
- Enterprise Security Architecture Program Development
- Enterprise SOC Framework and Incident Response Plan
- Enterprise International Security Partnerships Program Development
- Enterprise Security Assurance Program Development
- Enterprise Security Research Program Development
- Enterprise Information Security Product Strategy Development
- Enterprise Cyber Security Reporting
- Enterprise Cyber Insurance

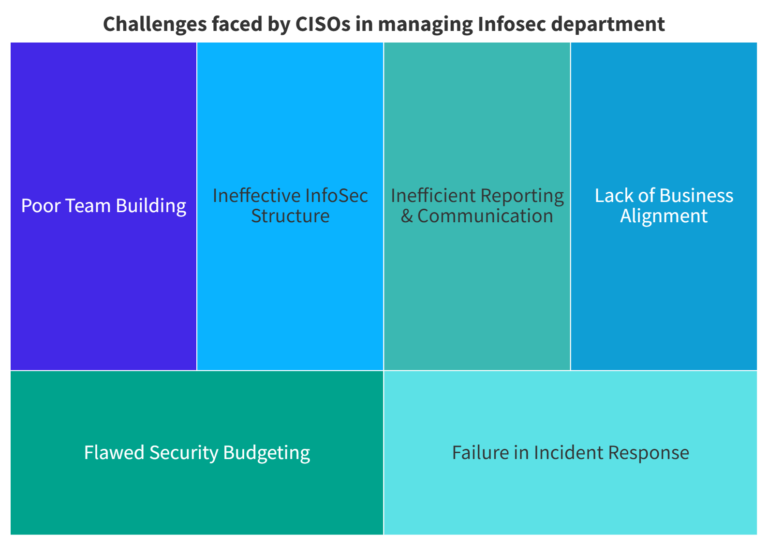
GRC Consulting and Program Development
Our Enterprise Risk Strategy ensures a structured approach to identifying, assessing, and mitigating cyber risks that impact business operations. We integrate governance, risk, and compliance (GRC) methodologies to enhance organizational resilience. By aligning security measures with business objectives, we help organizations stay ahead of evolving threats. Our strategy empowers decision-makers with risk intelligence for proactive cybersecurity management.
Enterprise Cyber Threat Profile Development
We develop a comprehensive cyber threat Profile by analyzing industry-specific risks and threat landscapes. Our approach includes threat intelligence integration, proactive defense mechanisms, and real-time threat monitoring. We map adversary tactics, techniques, and procedures (TTPs) to business-critical assets. Through a risk-based approach, we enhance security postures against sophisticated cyber threats.


Enterprise Cyber Risk Quantification and Cyber Security Budget Program Development
Our Cyber Security Budget Strategy helps organizations allocate resources effectively to maximize security investments. We conduct cyber risk quantification to prioritize spending on high-impact security controls. Through data-driven insights, we align security budgets with business objectives and regulatory requirements. This ensures cost-efficient, risk-based cybersecurity planning and financial resilience.
Enterprise Cyber Asset Attack Surface Management Program Development
We provide a structured approach to enterprise cyber asset attack surface management, ensuring visibility and protection of critical assets. Our strategy includes continuous asset discovery, risk assessment, and security posture evaluation. By identifying vulnerabilities in asset infrastructure, we help organizations mitigate potential attack vectors. Our proactive defense mechanisms strengthen resilience against unauthorized access and exploitation.


Enterprise Vulnerability Management Program Development
Our Enterprise Vulnerability Strategy focuses on proactive identification, assessment, and remediation of security weaknesses. We implement continuous vulnerability scanning, penetration testing, and risk-based patch management. By prioritizing vulnerabilities based on business impact, we ensure optimal resource allocation for remediation. Our approach strengthens organizations against emerging threats and exploits.
Enterprise Security Architecture Program Development
We design and implement robust security architectures tailored to enterprise needs, ensuring resilience against cyber threats. Our strategy includes Zero Trust frameworks, identity and access management (IAM), and network segmentation. We align security architecture with industry best practices and compliance mandates. This ensures a scalable, adaptive, and future-proof security posture.


Enterprise SOC Framework and Incident Response Plan
Our strategy establishes a structured and effective enterprise SOC framework and incident response plan. We ensure rapid threat detection, containment, and eradication through well-defined incident handling procedures. By implementing threat intelligence-driven response mechanisms, we minimize downtime and business impact. Our approach enhances organizational resilience against cyber incidents through continuous improvement.
Enterprise International Security Partnerships Program Development
We facilitate global cybersecurity partnerships, enabling enterprises to enhance their international security posture. Our strategy includes cross-border collaboration, compliance with international regulations, and threat intelligence sharing. By aligning security frameworks with global standards, we help organizations navigate complex security challenges. This approach strengthens enterprise resilience in an interconnected digital landscape.


Enterprise Security Assurance Program Development
Our Enterprise Security Validation Strategy ensures organizations maintain a high-security standard through rigorous assessment frameworks. We conduct red teaming, breach and attack simulations, and security posture evaluations. By validating security controls against real-world attack scenarios, we identify gaps and enhance defensive measures. This proactive approach helps organizations fortify their cybersecurity readiness.
Enterprise Security Research Program Development
We drive cutting-edge security research to stay ahead of evolving cyber threats and attack methodologies. Our research includes in-depth analysis of emerging threats, vulnerabilities, and adversarial tactics. By collaborating with industry leaders and regulatory bodies, we contribute to cybersecurity innovation. This research-driven approach empowers organizations with intelligence-led security strategies.


Enterprise Cyber Security Reporting
Our strategy ensures comprehensive cybersecurity reporting to provide stakeholders with actionable insights. We develop security dashboards, executive reports, and compliance-driven assessments. By integrating risk analytics and performance metrics, we help organizations track security effectiveness. Our reporting framework enhances decision-making and regulatory adherence through clear, data-driven security intelligence.



